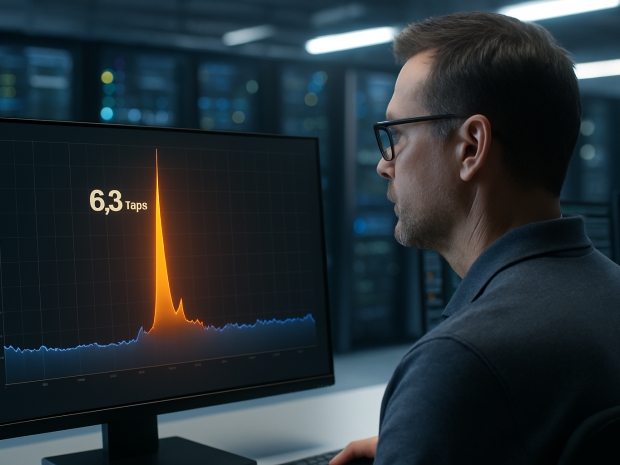
This latest attack lasted under a minute, pelting random UDP ports at 585 million packets per second. According to Google’s Damian Menscher, it was the biggest assault Project Shield has ever mitigated. Only Cloudflare has handled more traffic, with a 6.5 Tbps hit in April traced to the same source.
The culprit is Aisuru, a souped-up IoT botnet made from compromised routers, DVRs and other unsecured junk. The goal wasn’t to knock the site out, but to flex for potential customers sniffing around Telegram channels offering DDoS-as-a-service.
Running the show is Forky. He denies launching the attack, though admits to helping build and market the botnet. He claims to be just a support guy, focused on Botshield, his so-called DDoS mitigation business. The domain is tied to a Brazilian network engineer, Kaike Southier Leite, and a UK company fronted by a 21-year-old woman reportedly related to him.
Forky’s fingerprints are all over seized domains like stresser\[.]us and stresser\[.]best. He bragged about buying new ones hours after the FBI took them offline. DomainTools links his Botshield operation to several shady domains, including cant-mitigate\[.]us, using the same email address and Brazilian street address.
Forky insists he’s retired, but his Telegram chat history tells another story. He couldn’t explain away public posts from late 2024 showing him still neck-deep in the DDoS world. When asked who launched the May 12 attack, he first offered to find out, then said none of the “big guys” were stupid enough to do it.
Menscher reckons the Internet would be safer if Aisuru’s source code leaked. That would spawn clones, but also fragment its power. Mirai followed the same pattern after its code was dumped by its US authors, who were secretly running a DDoS-for-hire racket.
Until someone leaks Aisuru or exposes its exploit list, the game of whack-a-botnet continues. And Forky, true to form, remains right in the middle, claiming innocence while standing knee-deep in evidence.